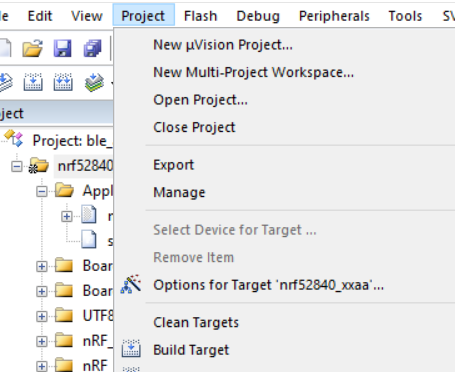
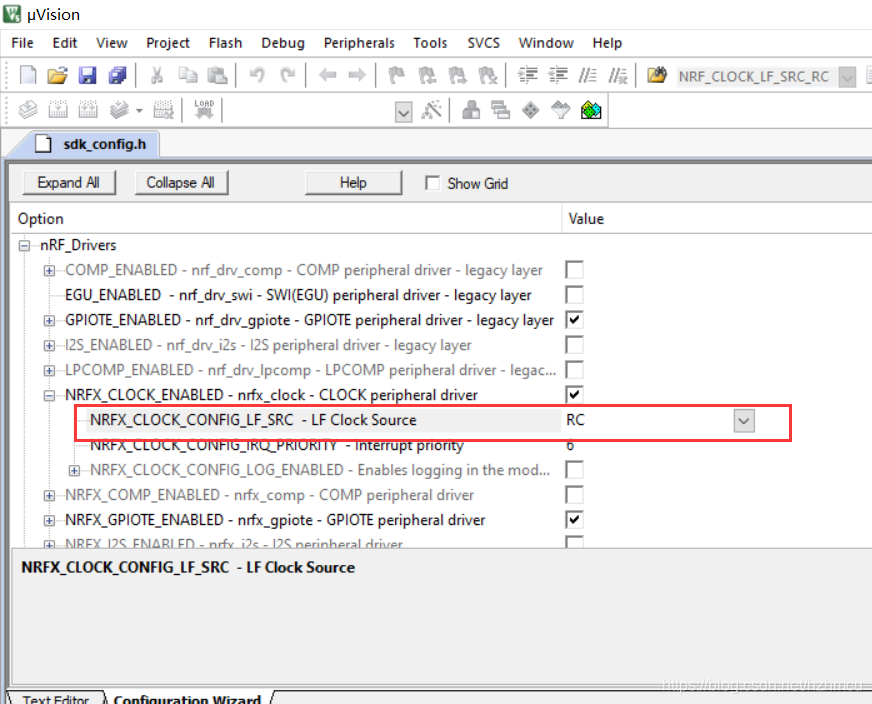
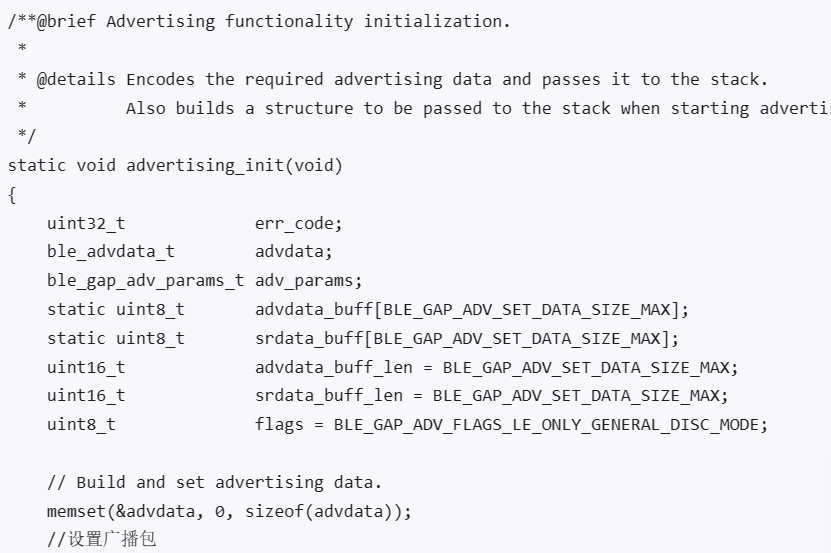
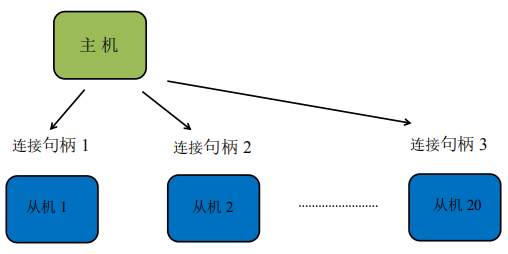
一、官方参考文档:
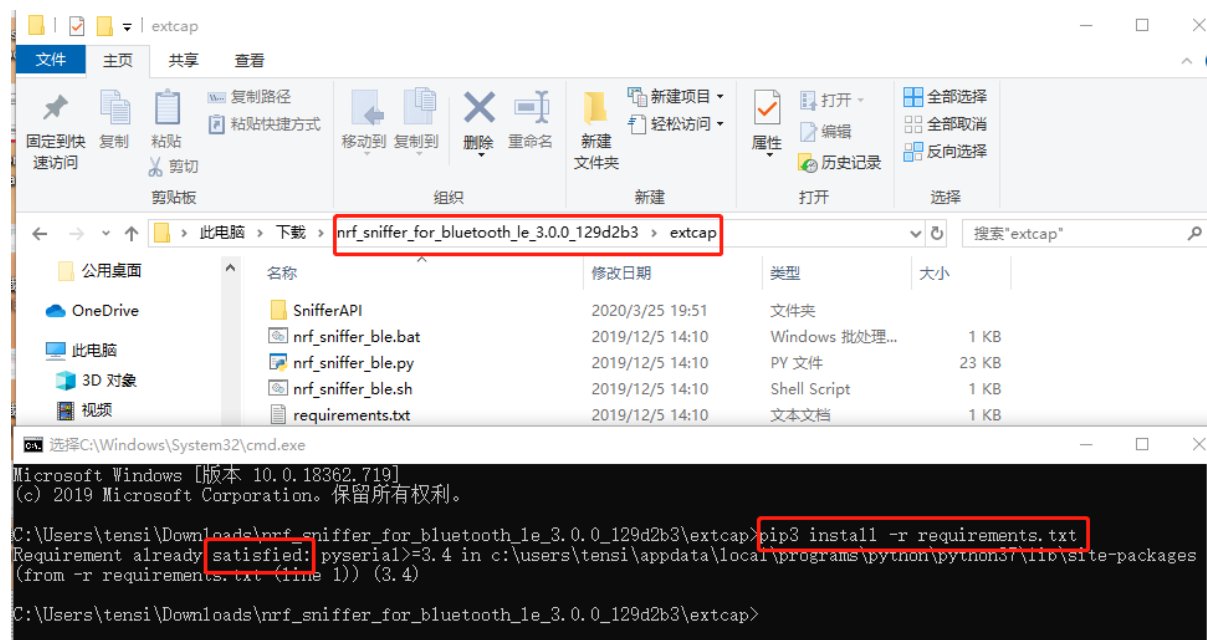
如果提示不认识命令pip3,可以将C:\Users\YGKJ\AppData\Local\Programs\Python\Python36\Scripts添加到系统变量的path中或者将这里边的pip3.exe拖到上面路径的CMD窗口运行安装即可。
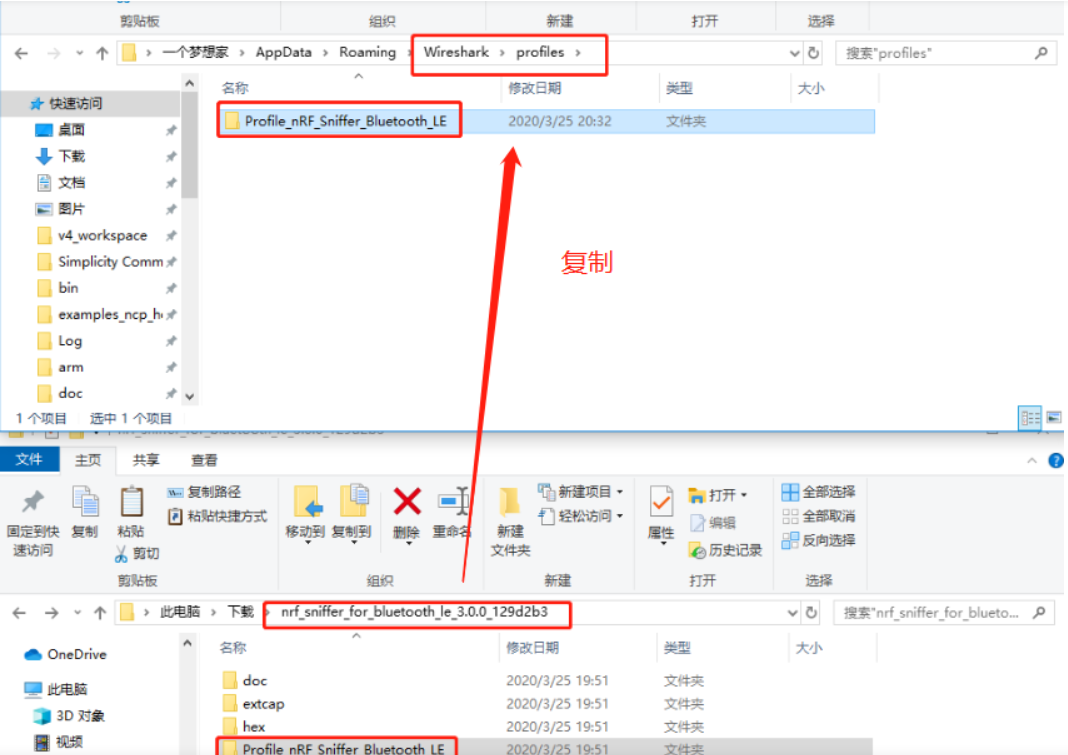
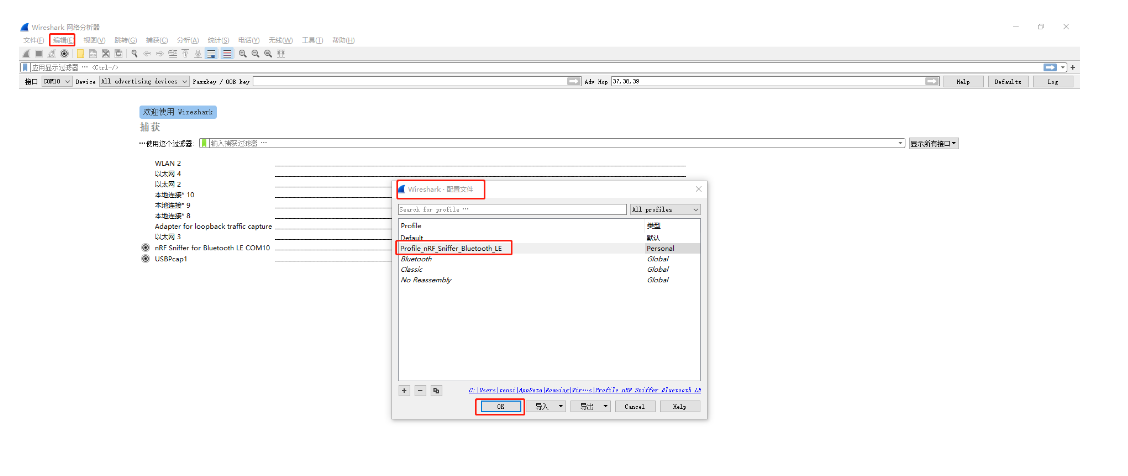
4.2安装和配置wireshark
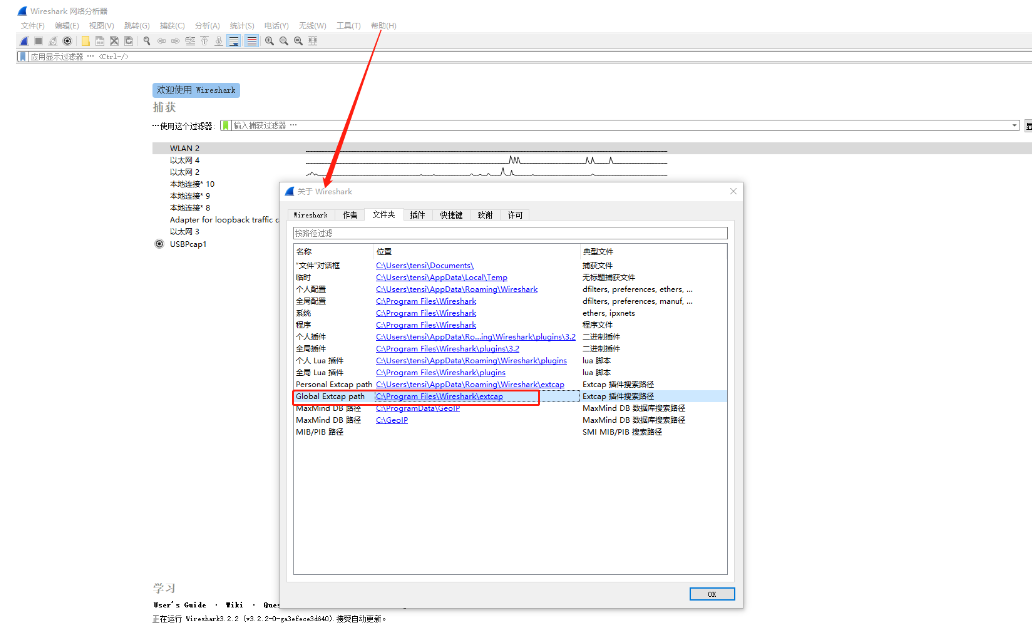
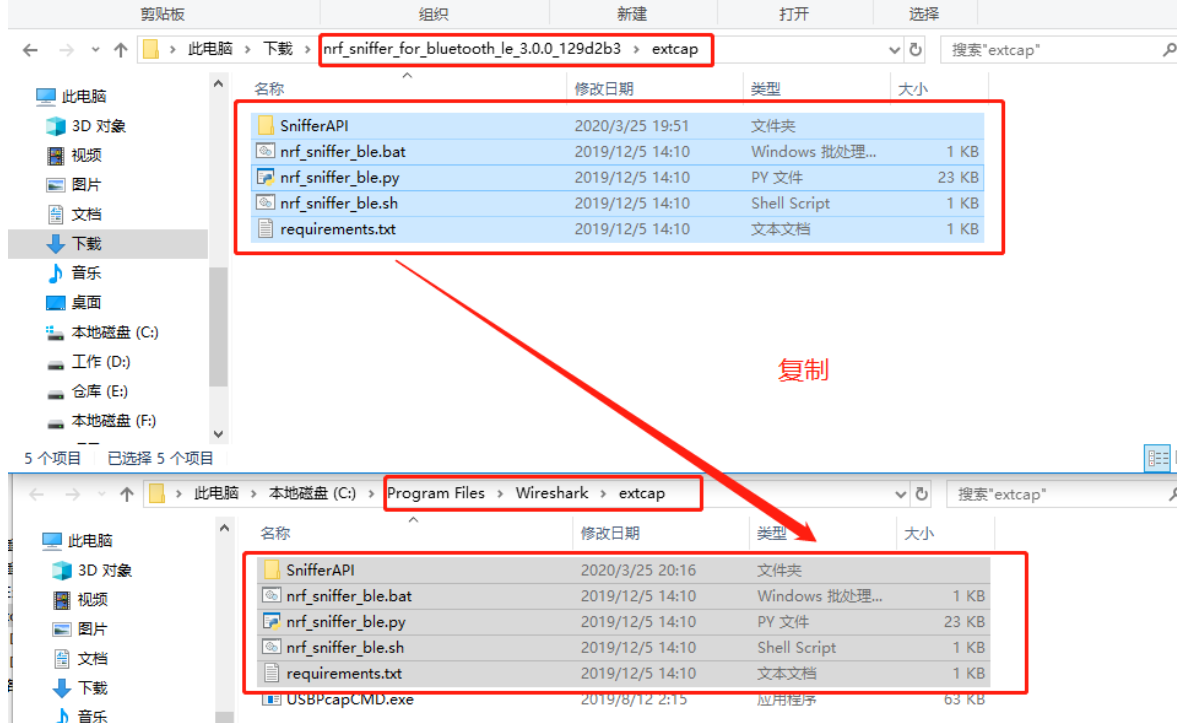
如果提示错误,则按照提示运行它提示的那个命令就行。
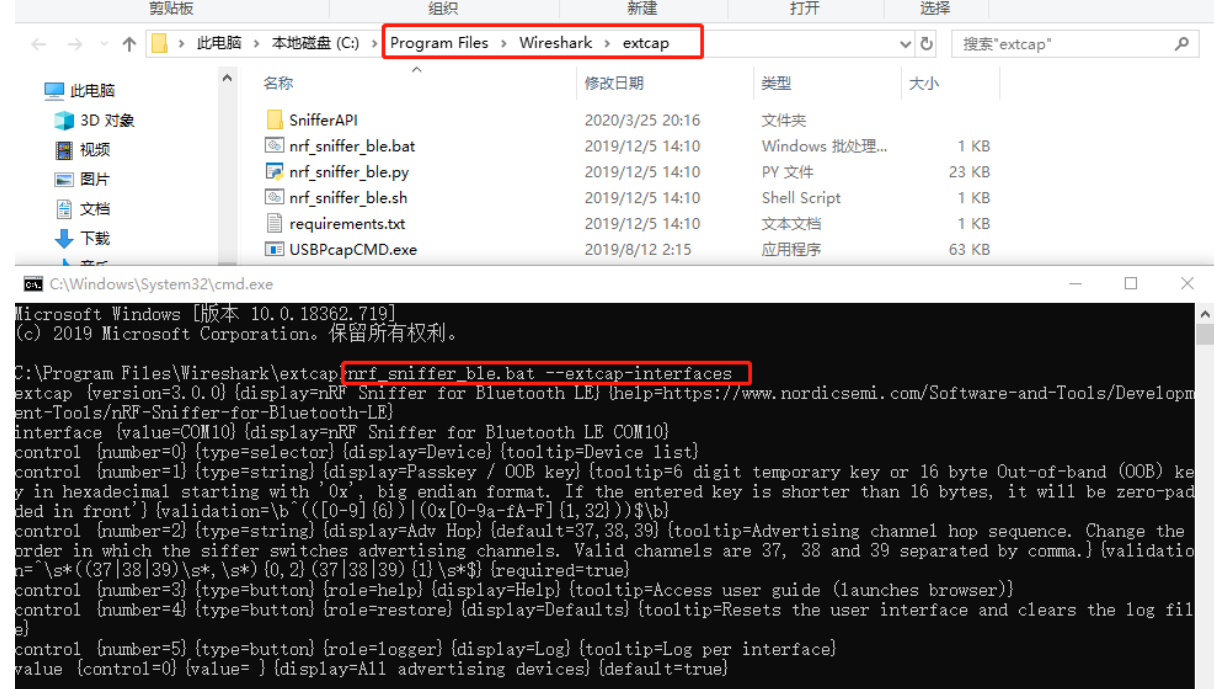
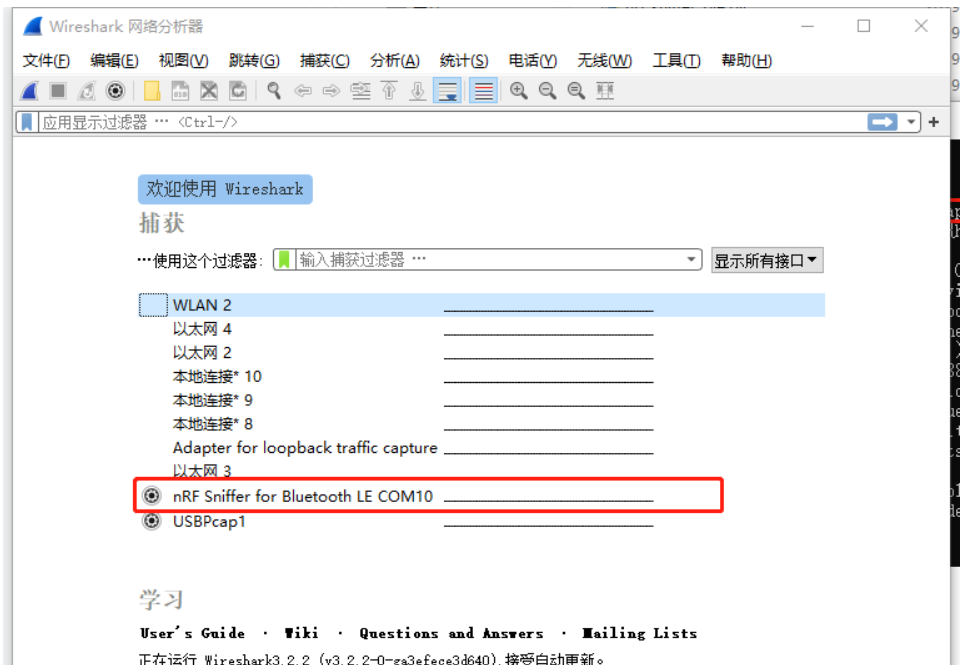
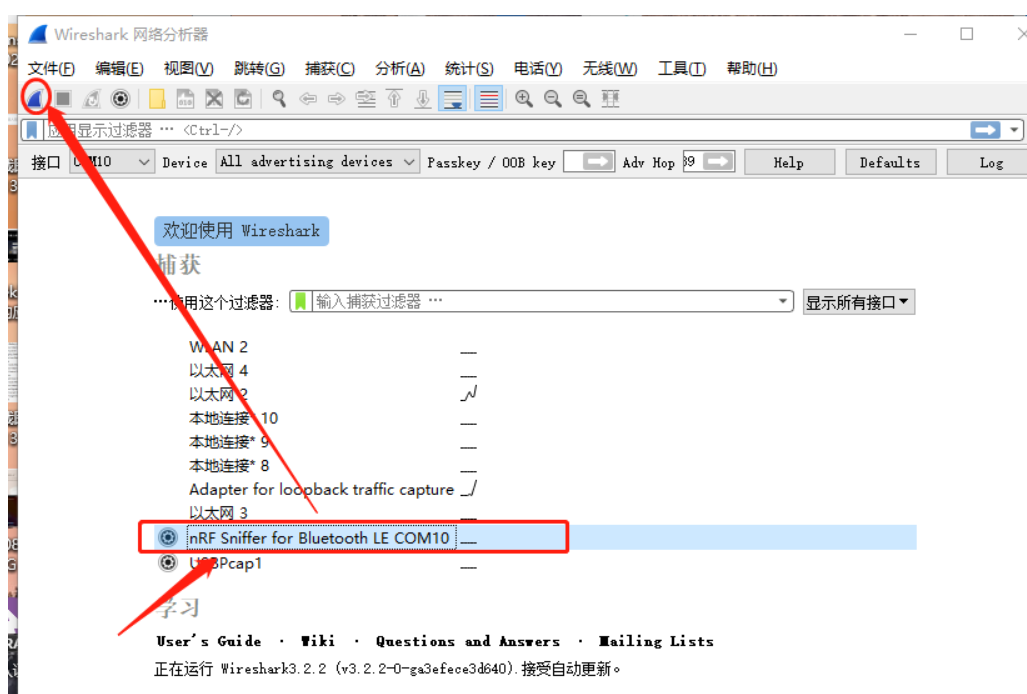
打开Wireshark软件,按F5刷新界面
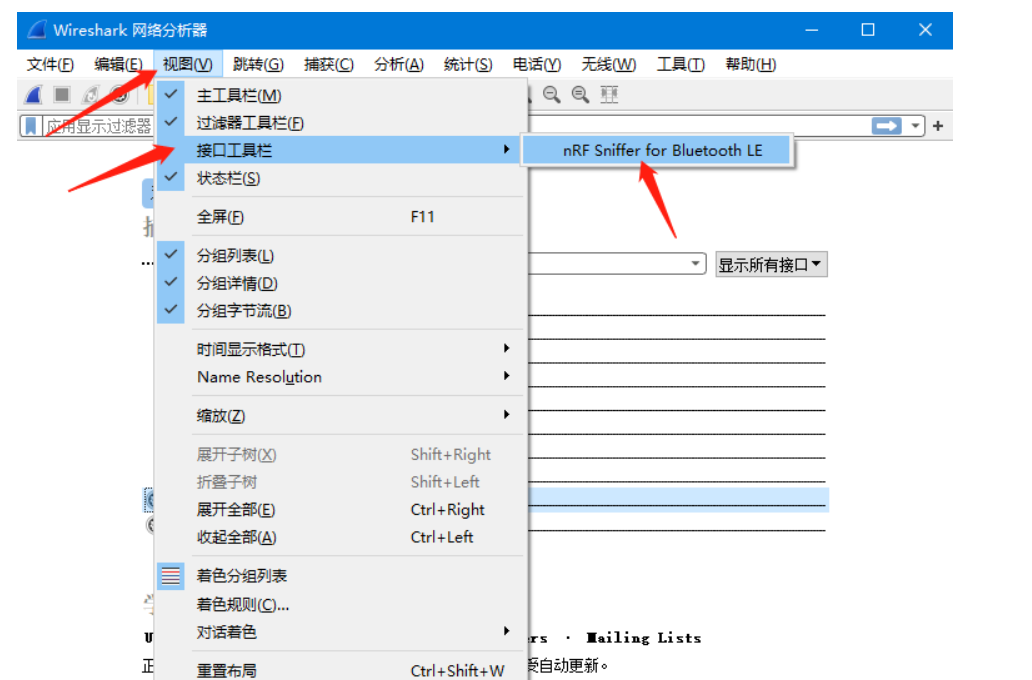
六、基本的用法
6.1 监听所有的蓝牙广播信道,尽可能多的从设备上获取蓝牙消息数据包,这是默认模式。
6.2 跟踪监听某一个特定的设备,并尝试捕获发送到该设备或从该设备发出的所有无线数据包。这个模式可以捕获以下几种数据包:
监听设备发出的蓝牙广播和扫描回复
监听设备收到的蓝牙扫描请求和连接请求
连接中两个设备之间发送的数据包
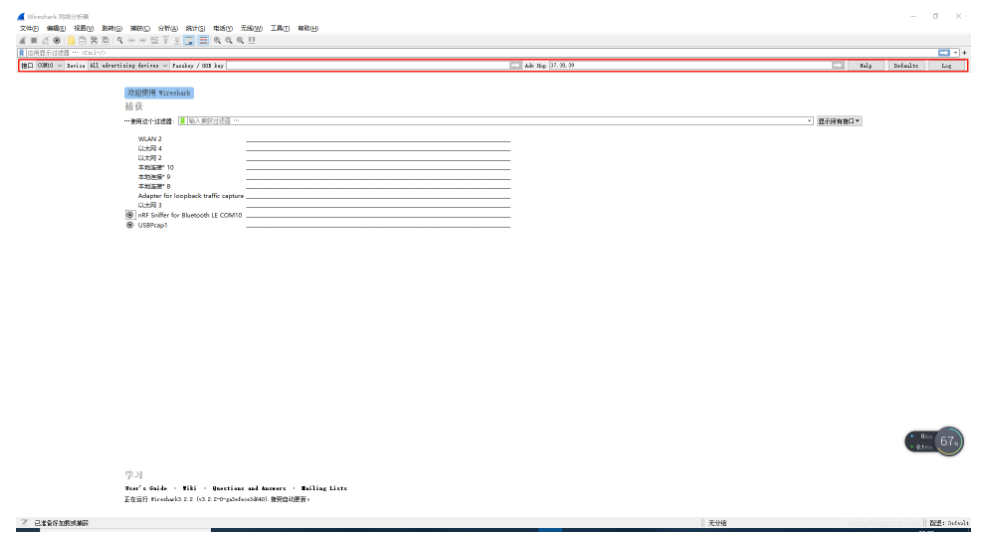
6.3选项
Hardware interface 抓包工具通道选择,可以同时选择多个
Device list 如果选择“All advertising devices”可以显示附近所有广播的设备消息,如果选择特定的某一个设备,就可以只监听这个设备的发送和接收
Passkey and OOB key 秘钥输入
Advertising hop sequence 广播调频顺序,默认顺序是37->38->39->37->38->39...,你可以自定义监听的顺序
RSSI filter 根据信号强度过滤 例如输入rssi >= -70
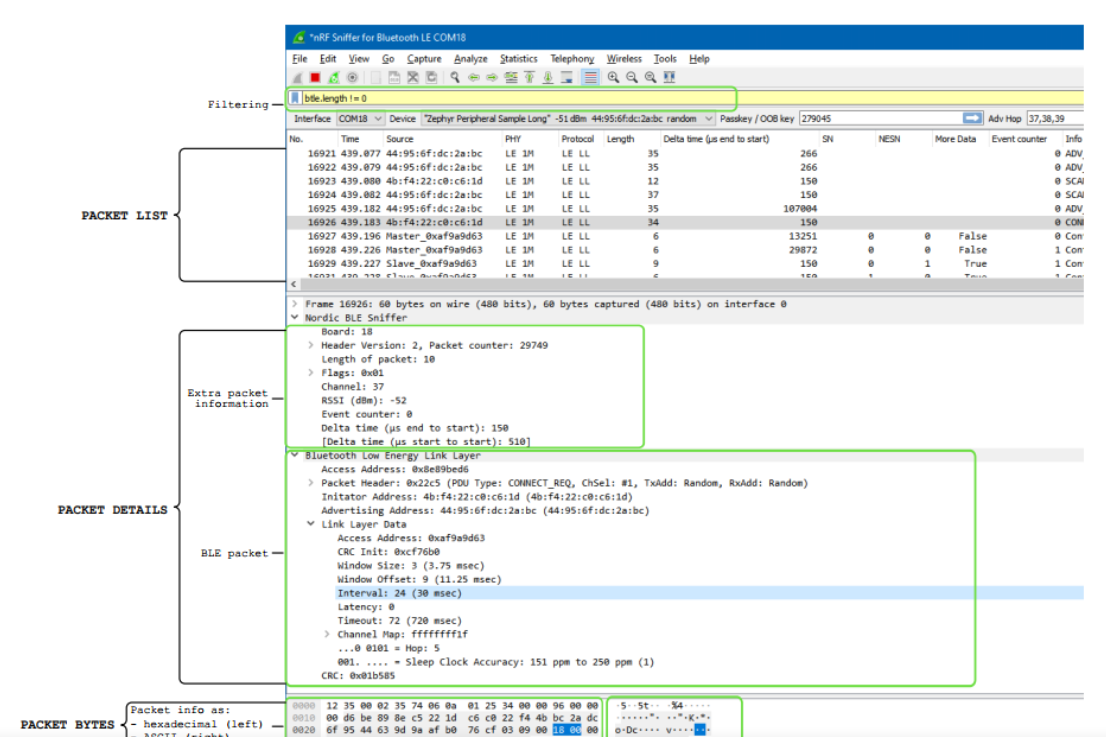
6.4 界面
6.5 抓包显示过滤
一般使用&& || == != !逻辑运算符过滤条件
6.6 添加信息显示列
6.7保存抓包文件和重新开始抓包
七、 抓包的几种场景
抓附近所有设备的广播数据包
Run nRF Sniffer (if not already running).
Ensure that All advertising devices is selected in the device list
抓某个特定的设备的数据包
Run nRF Sniffer (if not already running).
Select your device from the device list.
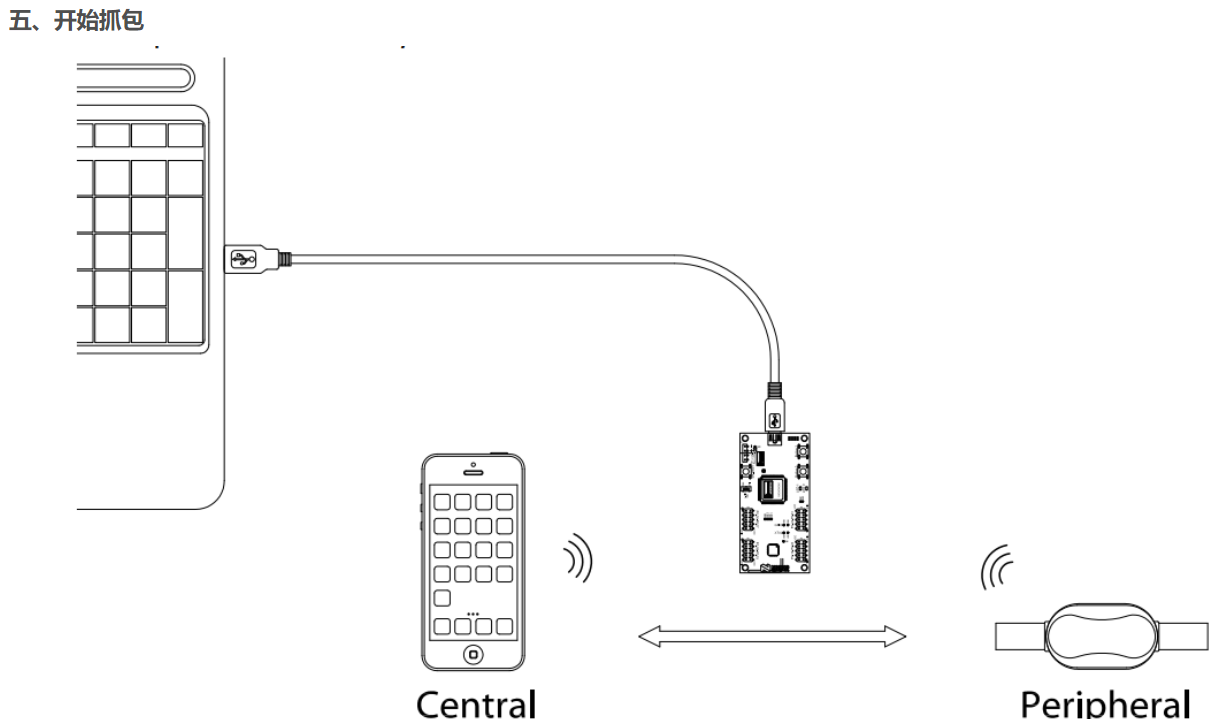
抓蓝牙连接过程的数据包
Run nRF Sniffer (if not already running).
Select your device from the device list.
Connect the Central to the Peripheral.
抓已经配对的设备间的数据包
Run nRF Sniffer (if not already running).
Select your device from the device list.
Enter the credentials for pairing. The procedure depends on the type of encryption.
• For connections that use legacy pairing with Just Works:
a. Initiate pairing between the devices if it does not happen automatically.
No further action is required.
• For connections that use legacy pairing with a passkey:
a. Initiate pairing between the devices if it does not happen automatically.
Common sniffing actions
b. Type the 6-digit passkey that is displayed on either the Central or the Peripheral device into the
Passkey / OOB key field in Wireshark.
c. Press Enter.
d. Enter the passkey into the other device.
• For connections that use legacy pairing with OOB:
a. Before the devices initiate pairing, type the OOB key in big-endian, hexadecimal format with a
leading "0x" into the Passkey / OOB key field in Wireshark.
b. Press Enter.
c. Connect the Central to the Peripheral device.
d. Initiate pairing between the devices if it does not happen automatically.
• For connections that use LE Secure Connections:
a. Enable Secure Connections debug mode on one or both of the devices.
b. Initiate pairing between the devices if it does not happen automatically.
In debug mode, the connection uses the debug keys specified in the Bluetooth Core Specification.
The Sniffer uses the same keys to decrypt the encrypted packets.